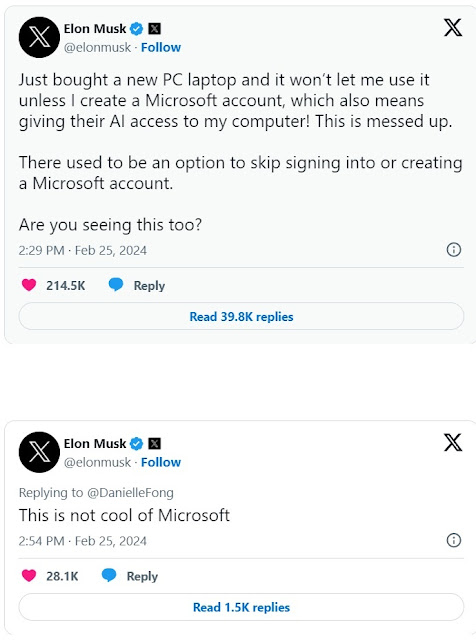
Gmail Scam So another kind of scam to get your Gmail credentials. Got this email from some vague email address claiming to be from Google. Link to unsubscribe takes you to a phishing web page wanting you to enter your Gmail User name & password. It's obvious one who falls for it will enter correct User name & Password which will be recorded by the attacker and you might get some error or confirmation so you try again. Meanwhile damage is already done and they have your correct info. These attacks come in different forms like this email or an eVite or some crazy offer which is too good to be true. So be careful and take your time and extra caution before hitting any link. If you are not sure about it just don't do it. There are some tweaks & settings which we implement on the PCs & Macs we work on like changing default DNS, adding Extensions to the Browser and changing some default policies to prevent such attacks. As the saying goes, "Prevention is Alw...